Researchers from the Netherlands discovered several vulnerabilities in various SSDs from Crucial and Samsung. The embedded hardware encryption can be bypassed.
Before we begin, the researchers have only tested a small number of Samsung and Crucial SSDs, it's likely more widespread to other brands as well. They gents not only have they been able to bypass encryption, they also simply download the firmware, reverse engineered it and found out how the security measures work for the SSD manufacturers. Carlo Meijer and Bernard van Gastel explain that the hardware data encryption technologies built into modern SSDs is easy to bypass making even Bitlocker ineffective. SSDs use native encryption solutions like AES and the researchers found that many hardware implementations with native encryption reveal security weaknesses, allowing for complete recovery of the data. They have published a paper on their findings which you can read here, Samsung already responded with an online notice.
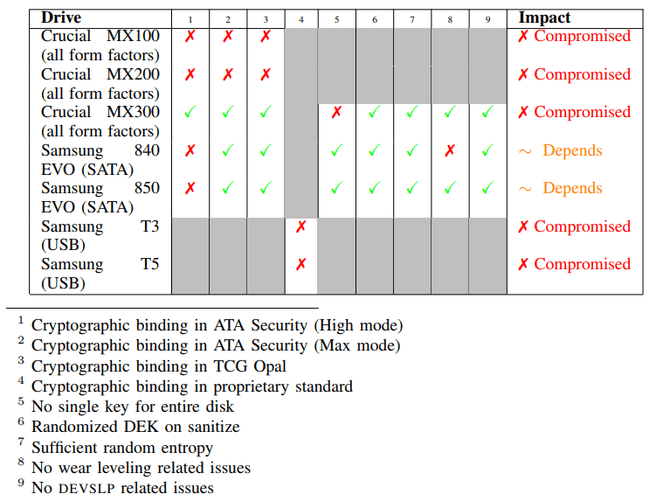
Vulnerability CVE-2018-12037 shows up on the Crucial MX100, MX200 and MX300, the external Samsung T3 and T5 ssds and the Samsung 840 Evo and 850 Evo. The researchers obtained the right entry to security, by buffer overflows and the JTAG debug interface. According to Van Gastel, there are also other ways of enabling the execution of code on the controller, such as via power glitching. Vulnerability, CVE-2018-12038 shows an issue with wear leveling at the chip on which the key is stored. SSDs are delivered without a password at factory default, by default everything is encrypted with the key stored unprotected. When changing a password, a protected key is still written, but due to wear leveling, the unprotected data could still reside on other sectors. The key without a password can thus be read in that other location, although it is logically impossible to extract it. This was the case with the Samsung 840 Evo. The researchers warn that Windows BitLocker can automatically choose hardware encryption if a drive with TCG Opal support is present. Only a completely new installation, with reformatting the disk, forces software encryption. "The command to see if Windows outsources the encryption to the disk is' manage-bde-status' in the Command Prompt or PowerShell. If 'Hardware Encryption' is behind 'Encryption Method', the encryption will be outsourced to the SSDs', according to Van Gastel.
The flaws can be found in the encryption mechanism of various types of solid state drives (SSDs) (listed below) by two major manufacturers, namely Samsung and Crucial. The vulnerabilities occur both in internal storage devices (in laptops, tablets and computers) and in external storage devices (connected via a USB cable). The affected storage media include popular models that are currently sold a lot. Researcher Bernard van Gastel: "The manufacturers involved were informed half a year ago in accordance with current professional practice. The results will be made public today so that organizations and consumers involved can protect their data properly. '
Researcher Carlo Meijer: 'This problem mainly requires action from organizations that store sensitive data on these devices. And also of some consumers who use this form of data protection. However, most consumers do not yet use this form of data protection. '
Recommendations
If sensitive data needs to be protected, it is advisable to use software encryption in any case and not only rely on hardware encryption. One of the possible options is to use the free VeraCrypt open source software package, but there are other solutions as well.
Background
Encryption (encryption) is the most important mechanism for data protection. This can be done via software and via hardware, for example in SSDs. In modern operating systems, software encryption is generally used for the entire storage. However, it is possible that such a control system decides to rely solely on hardware encryption (if supported by their storage medium via the TCG Opal standard). BitLocker, the encryption software built into Microsoft Windows, can make such a switch to hardware encryption, but in these cases it does not offer effective protection. Encryption software built into other operating systems (such as macOS, iOS, Android and Linux) seems unaffected when these switches are not executed.
Methods used
The researchers found these vulnerabilities with the aid of public information and around € 100 of evaluation equipment. They bought the SSDs that they researched through the normal sales channels. The vulnerabilities are quite difficult to discover. However, once the nature of the vulnerabilities is known, there is a risk that exploitation of these defects will be automated by others, making abuse easier. The researchers at Radboud University will not release such exploitation resources.
Products involved
The models where actual vulnerabilities have been demonstrated are:
- the Crucial (Micron) MX100, MX200 and MX300 internal hard drives;
- the Samsung T3 and T5 external USB drives;
- the Samsung 840 EVO and 850 EVO internal hard drives.
Windows computers
On computers with Windows, a software component called BitLocker provides encryption of the data from the computer. Within Windows, the type of encryption that BitLocker uses is set via the so-called Group Policy. Only a completely new installation, including reformatting the internal drive, will force software encryption. Changing the default value does not solve the problem immediately because it does not re-encrypt existing data. More information about the Group Policy setting can be found in the left section below.
Responsible disclosure
Both manufacturers were informed in April 2018 via the National Cyber Security Center (NCSC). The university has provided the data to both manufacturers so that they can adjust their product. The manufacturers themselves will provide detailed information to their customers about the models concerned; the necessary links are at the bottom.
When discovering a security error, there is always the dilemma of how to deal with this information. Immediate publication of the data can encourage attacks and cause damage. Long-term secrecy of the error can mean that the necessary steps to prevent vulnerability are not taken while people and organizations are still at risk. In the security community, it is common practice to look for a certain balance and to wait for defects to be exposed up to 180 days after the manufacturer of the product concerned has been informed. This procedure of responsible disclosure is used by Radboud University as standard.
The protection of digital data has become a necessity, especially in the light of the new European general data protection regulation (AVG). Radboud University wants to contribute to this through its computer security research, both by developing new security mechanisms and by analyzing the power of existing mechanisms.
Publication
The researchers are now about to publish the scientific aspects of their findings in the scientific literature. Today, November 5, 2018, a preliminary version (pdf, 757 kB) of these findings will be published. After the end of the peer review process, a definitive version will appear in the scientific literature. This publication is not a guide to breaking into SSDs.
Researchers successfully bypass hardware encryption in Samsung and Crucial SSDs