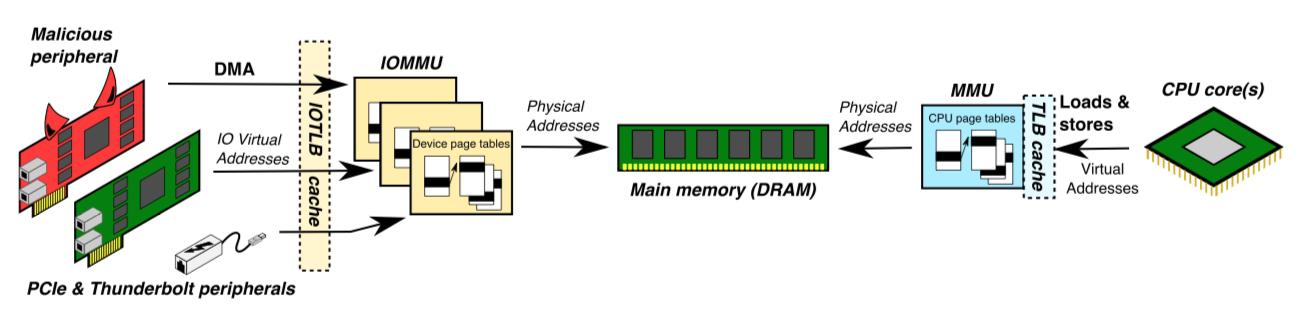
A big Vulnerability in Thunderbolt has surfaced, the researches call it Thunderclap (Vulnerability these days need to have a fancy name for some sort of reason). The vulnerability allows direct memory access attacks, or simply DMA attacks, to be carried out, which ensure that an attacker has unrestricted access to the memory.
Thunderbolt peripherals and accessories are effectively considered to be trusted components of a computer, complete with direct memory access that can bypass operating system security policies, according to security researcher Theo Markettos. Thunderbolt offers devices "more privilege than regular USB devices," giving them more freedom and access to potentially sensitive information.
The researchers say that most modern laptops, as well as a number of desktop computers, are susceptible to being vulnerable to Thunderclap-based attacks which can be carried out either with specially built malicious peripheral devices or common devices such as projectors or chargers that have been altered to automatically attack the host they are connected to. Even though most vendors have implemented Input-Output Memory Management Units (IOMMUs) designed to provide memory protection for DMA and block all memory access from unrecognized devices altogether.
In collaboration with the research team, OS vendors have also added Thunderclap mitigation measures to their platforms starting with 2016 but the measures are not 100% effective and security flaws still impact systems protected using IOMMU.
Thunderclap affects basically all operating systems—the researchers call out macOS, Windows, Linux, and FreeBSD—and all Macs released since 2011 other than the 12-inch MacBook, which has only USB-C.
The researchers have published their finding here in this PDF.
Vulnerability in Thunderbolt allows unlimited memory access