UEFI rootkits are widely viewed as extremely dangerous tools for implementing cyberattacks, as they are hard to detect and able to survive security measures such as operating system reinstallation and even a hard disk replacement. Some UEFI rootkits have been presented as proofs of concept; some are known to be at the disposal of (at least some) governmental agencies. However, no UEFI rootkit has ever been detected in the wild – until we discovered a campaign by the Sednit APT group that successfully deployed a malicious UEFI module on a victim’s system.
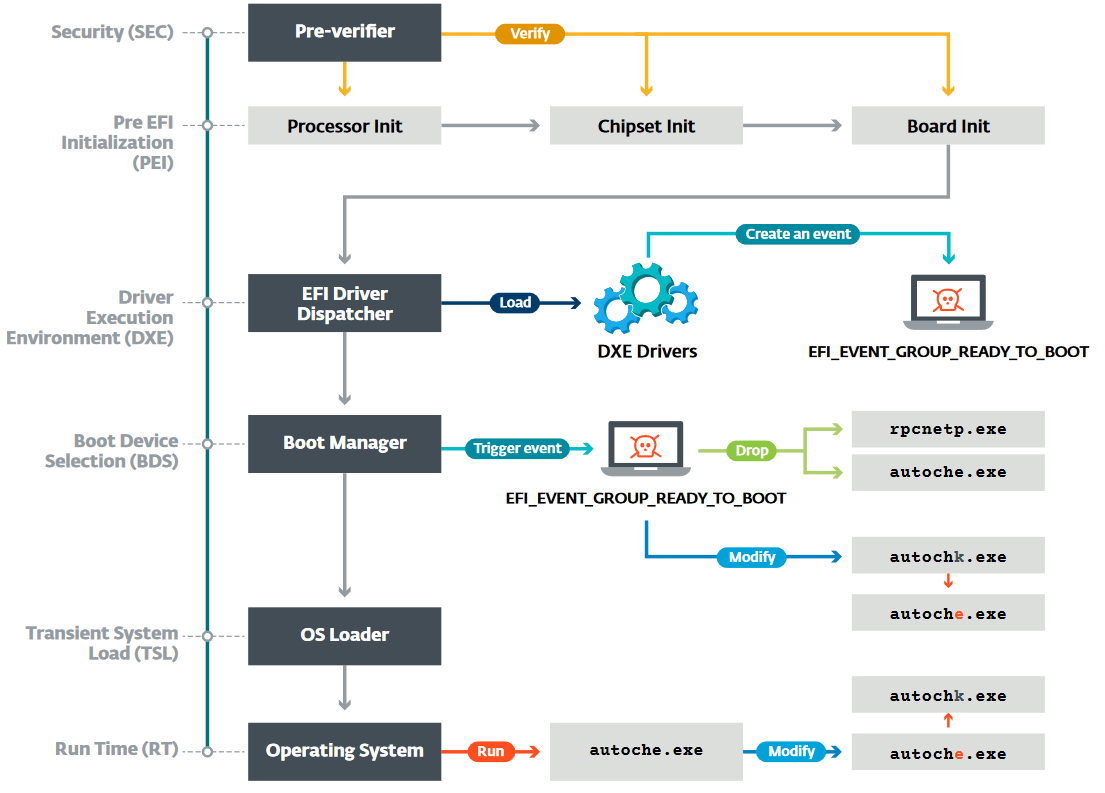
Security researchers explain that they found three different types of tools on a victim's computer. Two of them are responsible for gathering details about the system firmware and for creating a copy of the system firmware by reading the SPI flash memory module, where the UEFI firmware is located.
The last one injects the malicious module and writes the compromised firmware back to the SPI flash memory, creating persistence for the malware. To reach the UEFI/BIOS settings, all tools use the kernel driver of the RWEverything tool that allows modification of the settings in the firmware of almost any hardware. The driver is signed with a valid certificate. The purpose of the rootkit is just to drop malware into the Windows operating system and make sure that it executes at startup.
Protecting against LoJax infection is possible by enabling the Secure Boot mechanism, which checks that every component loaded by the system firmware is signed with a valid certificate. Since LoJax rootkit is not signed, Secure Boot can prevent it from dropping the malware in the first place. Another way to protect against Sednit's rootkit is to make sure the motherboard has the latest firmware version from the manufacturer. The patching tool can do its job only if the protections for the SPI flash module are vulnerable or misconfigured. An updated firmware should render fruitless the malicious update operation. Reflashing the firmware, however, is a task most users are unfamiliar with. It is a manual operation that typically involves downloading the latest firmware version from the motherboard manufacturer, saving it on an external storage device, booting into the UEFI menu and installing it.
How to protect yourself?
Sednit’s UEFI rootkit is not properly signed, so the first security mechanism that could have blocked such an attack is Secure Boot. When Secure Boot is enabled, each and every firmware component that is loaded by the firmware needs to be properly signed, thus ensuring the integrity of the firmware. We strongly suggest that you enable it. This is the base defense against attacks targeting UEFI firmware and can be enabled at boot time through your system’s UEFI settings.
Updating system firmware should not be something trivial for a malicious actor to achieve. There are different protections provided by the platform to prevent unauthorized writes to system SPI flash memory. The tool described above is able to update the system’s firmware only if the SPI flash memory protections are vulnerable or misconfigured. Thus, you should make sure that you are using the latest available UEFI/BIOS available for your motherboard. Also, as the exploited vulnerability affects only older chipsets, make sure that critical systems have modern chipsets with the Platform Controller Hub (introduced with Intel Series 5 chipsets in 2008).
Unfortunately for the ambitious end user, updating a system’s firmware is not a trivial task. Thus, firmware security is mostly in the hands of UEFI/BIOS vendors. The security mechanisms provided by the platform need to be configured properly by the system firmware in order to actually protect it. Firmware must be built from the ground up with security in mind. Fortunately, more and more security researchers are looking at firmware security, thus contributing to improving this area and raising awareness among UEFI/BIOS vendors.
Remediation of a UEFI firmware-based compromise is a hard problem. There are no easy ways to automatically remove such a threat from a system. In the case we described above: in order to remove the rootkit, the SPI flash memory needs to be reflashed with a clean firmware image specific to the motherboard. This is a delicate operation that must be performed manually. It is definitely not a procedure that most computer owners are familiar with. The only alternative to reflashing the UEFI/BIOS is to replace the motherboard of the compromised system outright.