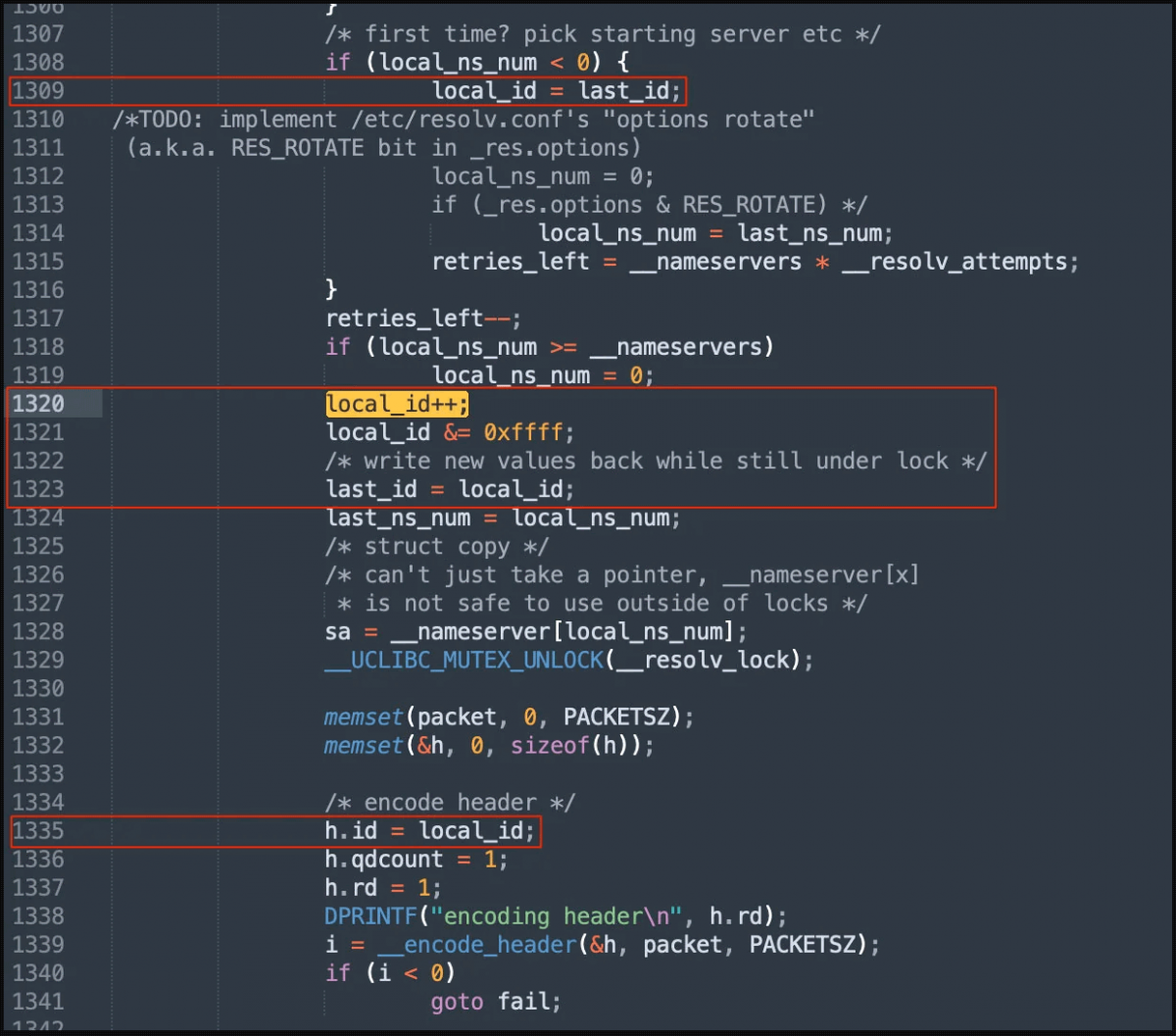
An unresolved DNS vulnerability affects millions of Linksys and Netgear routers, as well as other IoT equipment. Nozomi Networks Labs security researchers found CVE-2022-05-02, a DNS implementation flaw in two prominent C libraries. uClibc and uClibc-ng are commonly found in routers and IoT devices.
DNS poisoning is essentially fooling the target device into pointing to an arbitrarily defined endpoint and communicating with it over the network. The attacker would then be able to divert traffic to a server under their direct control. A threat actor can employ DNS poisoning or DNS spoofing to send the victim to a malicious website hosted at an IP address on the attacker's server rather than the genuine destination. The OpenWRT team's fork, uClibc-ng, and the library uClibc. Both types are extensively utilized by major companies like as Netgear, Axis, and Linksys, as well as embedded Linux releases. According to Nozomi Networks experts, a remedy from the uClibc developer is not yet available, putting products from up to 200 companies at risk.
- "Because this vulnerability remains unpatched, for the safety of the community, we cannot disclose the specific devices we tested on," says Nozomi
- "We can, however, disclose that they were a range of well-known IoT devices running the latest firmware versions with a high chance of them being deployed throughout all critical infrastructure."
Users of IoT and router devices should keep a lookout for new firmware releases from suppliers and install the most recent upgrades as soon as they are available.
Millions Linksys and Netgear other routers and IoT devices are vulnerable to DNS poisoning