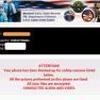
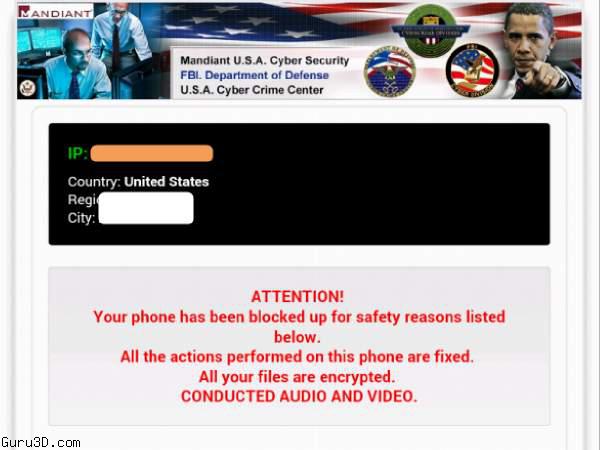
Quick, pay this fine or the FBI will arrest you! That's how a new type of Android ransomware is tricking people into paying up. Once installed, the malware, dubbed "Koler.A," locks up the phone, preventing users from accessing the home screen and effectively holding the phones ransom until users pay $300. "Koler.A," first detected Sunday (May 4) by the pseudonymous French security blogger Kafeine, is one of the first discovered examples of Android ransomware, and the first known "police Trojan" for Android. Fortunately, its bark is worse than its bite.
Koler.A spreads using malicious traffic-distribution systems (TDS) — short pieces of software placed on websites, often through ads, that redirect visitors to other sites. Malicious TDS's detect visitors' browsers, operating systems and countries of residence, and redirect them to malicious Web pages with embedded browser exploit kits tailored to each victim. In the case of Android devices, the visitor's browser will be redirected to a fake pornography website that will try to trigger a drive-by download (which won't work if the device is set to reject any app from outside the Google Play store).
However, even if the download succeeds, the Android user will have to manually approve the app's installation. The malware creators have to trick users into thinking the malicious app is harmless. How do the ransomware creators trick these discerning porn site visitors? By promising more porn, of course! Kolar.A presents itself as BaDoink, a video player app that often needs to be installed to view streaming porn on mobile devices.
Cryptolocker Like Ransomware Spreads to Android Devices