There is a form of ransomware exploiting a vulnerable Gigabyte driver. since the driver is digitally signed it becomes easy to install. The malware installs a second driver that disables security software, after which the encryption begins.
The signed driver, part of a now-deprecated software package published by Taiwan-based motherboard manufacturer Gigabyte, has a known vulnerability, tracked as CVE-2018-19320. The problem is a kernel driver called gdrv .sys that is prone to escalation privilege . Although the driver is no longer being used, it is still digitally approved by Versign, why this is the case is not yet known. Thanks to this certificate, the driver can still be installed, after which Windows driver signature verification can be disabled.
The vulnerability, published along with proof-of-concept code in 2018 and widely reported at the time, was disclaimed by the company, who told the researcher who tried to report the bug that “its products are not affected by the reported vulnerabilities.” The company later recanted, and has discontinued using the vulnerable driver, but it still exists, and it apparently remains a threat. Verisign, whose code signing mechanism was used to digitally sign the driver, has not revoked the signing certificate, so the Authenticode signature remains valid. In this attack scenario, the criminals have used the Gigabyte driver as a wedge so they could load a second, unsigned driver into Windows. This second driver then goes to great lengths to kill processes and files belonging to endpoint security products, bypassing tamper protection, to enable the ransomware to attack without interference.
Known Affected Software Configurations
| cpe:2.3:a:gigabyte:aorus_graphics_engine:*:*:*:*:*:*:*:* Show Matching CPE(s) |
Up to (including) 1.33 |
|
| cpe:2.3:a:gigabyte:app_center:*:*:*:*:*:*:*:* Show Matching CPE(s) |
Up to (including) 1.05.21 |
|
| cpe:2.3:a:gigabyte:oc_guru_ii:2.08:*:*:*:*:*:*:* Show Matching CPE(s) |
||
| cpe:2.3:a:gigabyte:xtreme_gaming_engine:*:*:*:*:*:*:*:* Show Matching CPE(s) |
Up to (including) 1.25 |
|
The vulnerability is active throughout the entire software suite
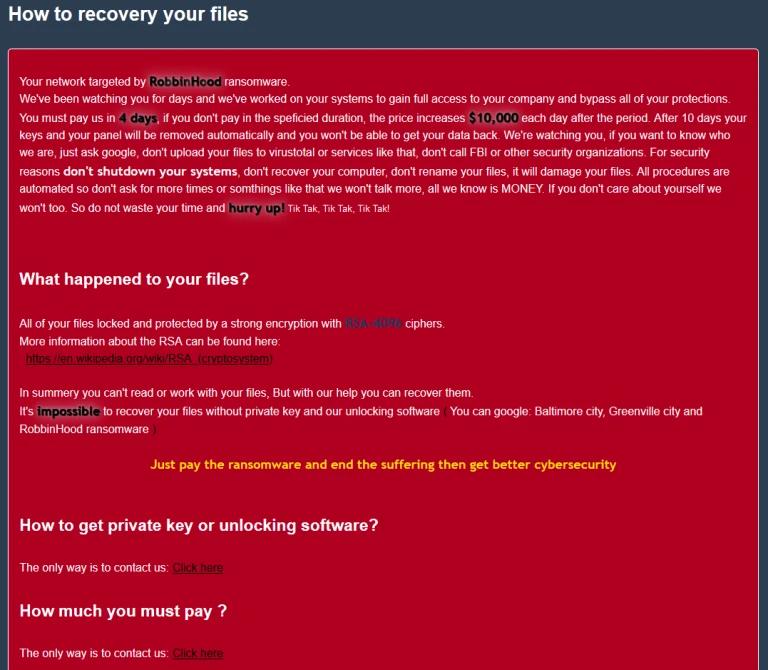
It is the first time we have observed ransomware shipping a trusted, signed (yet vulnerable) third party driver to patch the Windows kernel in-memory, load their own unsigned malicious driver, and take out security applications from kernel space. The ransomware that was being installed in both instances calls itself RobbinHood.
Gigabyte earlier on Gigabyte claimed its products were not affected.
Read more on sophos.
Vulnerable yet digitally signed Gigabyte driver actively being exploited - RobbinHood Randomware