Let's face it, UEFI, in your BIOS is a little operating system on its own, completely unprotected. Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) is extending its protection capabilities to the firmware level with a new Unified Extensible Firmware Interface (UEFI) scanner.
The Unified Extensible Firmware Interface (UEFI) is a replacement for legacy BIOS. If the chipset is configured correctly (UEFI & chipset configuration itself) and secure boot is enabled, the firmware is reasonably secure. To perform a hardware-based attack, attackers exploit a vulnerable firmware or a misconfigured machine to deploy a rootkit, which allows attackers to gain foothold on the machine.
Hardware and firmware-level attacks have continued to rise in recent years, as modern security solutions made persistence and detection evasion on the operating system more difficult. Attackers compromise the boot flow to achieve low-level malware behavior that’s hard to detect, posing a significant risk to an organization’s security posture.
Windows Defender System Guard helps defend against firmware attacks by providing guarantees for secure boot through hardware-backed security features like hypervisor-level attestation and Secure Launch, also known as Dynamic Root of Trust (DRTM), which are enabled by default in Secured-core PCs. The new UEFI scan engine in Microsoft Defender ATP expands on these protections by making firmware scanning broadly available.
The UEFI scanner is a new component of the built-in antivirus solution on Windows 10 and gives Microsoft Defender ATP the unique ability to scan inside of the firmware filesystem and perform security assessment. It integrates insights from our partner chipset manufacturers and further expands the comprehensive endpoint protection provided by Microsoft Defender ATP.
The new UEFI scanner reads the firmware file system at runtime by interacting with the motherboard chipset. To detect threats, it performs dynamic analysis using multiple new solution components that include:
- UEFI anti-rootkit, which reaches the firmware through Serial Peripheral Interface (SPI)
- Full filesystem scanner, which analyzes content inside the firmware
- Detection engine, which identifies exploits and malicious behaviors
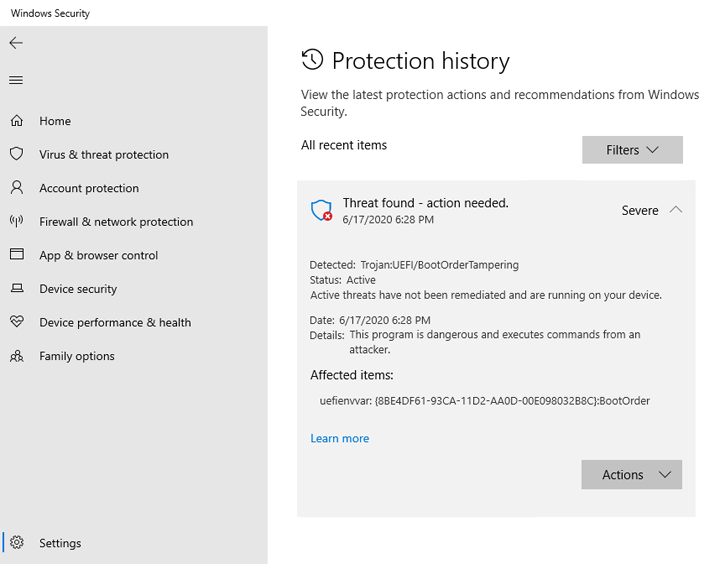
Firmware scanning is orchestrated by runtime events like suspicious driver load and through periodic system scans. Detections are reported in Windows Security, under Protection history.
Microsoft Defender ATP customers will also see these detections raised as alerts in Microsoft Defender Security Center, empowering security operations teams to investigate and respond to firmware attacks and suspicious activities at the firmware level in their environments.
To detect unknown threats in SPI flash, signals from the UEFI scanner are analyzed to identify anomalies and where they have been executed. Anomalies are reported to the Microsoft Defender Security Center for investigation. Thanks, Watcher for the news submit.