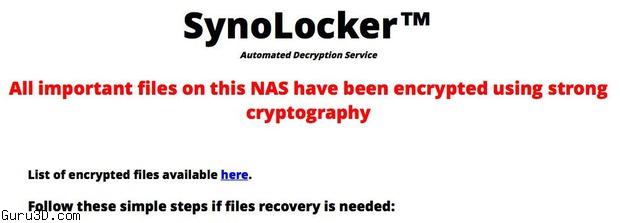
Multiple users of the popular Synology NAS are complaining that their NAS unit was infected with Ransomware, encrypting their data rendering it as inaccessible. A new malware called Synolocker encrypts all files on the NAS server, if users want their data unlocked they will have to pay hundreds of Euros to retrieve their files.
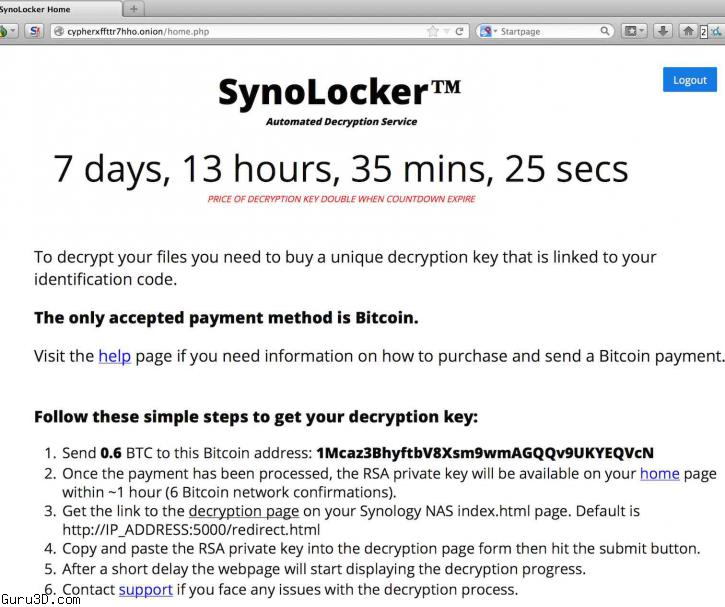
End-users are complaining on the Synology forum that they can not access their data anymore and to unlock / decrypt the data again, they are forced to pay 0,6 Bitcoin (260 EURO) to regain access through a TOR hidden website. To this point it is unclear if in fact the end-users can access the data again after they paid.
Synolocker seems to resemble CryptoLocker a lot, the dreaded ransomware that effected many user. Up-to this moment it is unclear how Synolocker installs itself, it could be through a leak in the user interface, hacked SSH or even FTP. Often it is the result not updating firmware in combination with exposing the NAS units to the world wide web. Rumored right now is that users effected have an old DSM for which heartbleed was not fixed. Others claim that the NAS'es infected all had EZ-Internet service enabled.
For now we would like to advice to take your Synology NAS offline until Synology releases an explanation, typically they are very fast with their fixes. But do not allow your NAS to be publicly reached over your router to the internet. Also make sure you have the latest firmware of your Synology NAS server installed.
Earlier this year Synology NAS systems have been abused to mine bitcoins and dogecoins. it is claimed that the attackers have been able to mine up-to half a million EURO.
Update:
The issue is currently localized to NAS units running non-updated versions of DSM 4.3, but Synology is investigating if the hack works on DSM 5.0 as well.
Synology is urging users to take the following steps - close all ports for external (Internet) access, and unplug your NAS from your local network; and with your NAS plugged into just one machine, update DSM to the latest version; and back-up your data. If your NAS unit is infected, disconnect it from the network, perform a hard-shutdown, and contact Synology. The issue highlights one of the many dangers of a distributed currency, in which the beneficiary of funds is difficult to trace.
Here's an emergency statement from Synology (the company is preparing a press-release):
You may have heard by now that DSM is undergoing a CryptoLocker hack called SynoLocker – as of yesterday (08/03/14). It’s a BitCoin Mining hack that encrypts portions of data, and ransoms the decryption key for .6 BitCoin ($350). So far, it looks like the matter is localized to non-updated versions of DSM 4.3, but we are actively working on, and researching the issue to see if it also effects DSM 5.0 as well.
In the interim, we are asking people to take the following precautions:
A. Close all open ports for external access as soon as possible, and/or unplug your Disk/RackStation from your router
B. Update DSM to the latest version
C. Backup your data as soon as possible
D. Synology will provide further information as soon as it is available.
If your NAS has been infected:
A. Do not trust/ignore any email from unauthorized/non-genuine Synology email. Synology email always has the “synology.com” address suffix.
B. Do a hard shutdown of your Disk/RackStation to prevent any further issues. This entails a long-press of your unit’s power button, until a long beep has been heard. The unit will shut itself down safely from that point.
C. Contact Synology Support as soon as possible at, http://www.synology.com/en-global/support/knowledge_base
Update 2:
Synology has been investigating and working with users affected by a recent ransomware called "SynoLocker." Synology has confirmed the ransomware affects Synology NAS servers running older versions of DiskStation Manager, by exploiting a vulnerability that was fixed in December, 2013, at which time Synology released patched software and notified users to update via various channels.
Affected users may encounter the following symptoms:
- When attempting to log in to DSM, a screen appears informing users that data has been encrypted and a fee is required to unlock data.
- Abnormally high CPU usage or a running process called "synosync" (which can be checked at Main Menu > Resource Monitor).
- DSM 4.3-3810 or earlier; DSM 4.2-3236 or earlier; DSM 4.1-2851 or earlier; DSM 4.0-2257 or earlier is installed, but the system says no updates are available at Control Panel > DSM Update.
For users who have encountered the above symptoms, please shutdown the system immediately to avoid more files from being encrypted and contact our technical support here. However, Synology is unable to decrypt files that have already been encrypted.
For other users who have not encountered the above symptoms, Synology strongly recommend downloading and installing DSM 5.0, or any version below:Users can manually download the latest version from our Download Center and install it at Control Panel > DSM Update > Manual DSM Update.
- DSM 4.3-3827 or later
- DSM 4.2-3243 or later
- DSM 4.0-2259 or later
- DSM 3.x or earlier is not affected
Synology sincerely apologizes for any problems or inconvenience this issue has caused our users. As cybercrime proliferates and increasingly sophisticated malware evolves, Synology continues to devote resources to mitigate threats and is dedicated to providing users with reliable solutions.