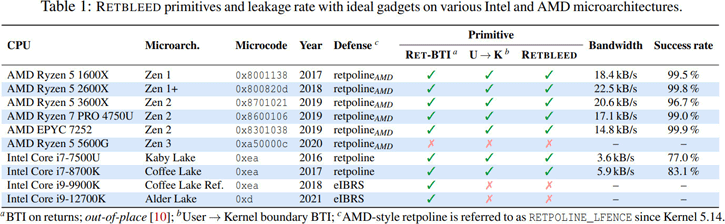
Investigators from the Swiss university ETH Zurich have discovered a new Spectre-like vulnerability that takes use of the processor's speculative execution to get access to sensitive data. Retbleed impacts AMD Ryzen processors up to and including Zen 2, whereas Intel CPUs in the 7000 and 8000 series are affected.
Despite existing safeguards, older AMD and Intel CPUs are susceptible to yet another Spectre-based speculative-execution attack that exposes secrets inside kernel memory. It is believed that mitigating this side channel would have an impact on performance. In summary, rogue software on a computer may use Retbleed to get passwords, keys, and other secrets from memory that it shouldn't have access to, such as operating system kernel data. As with other Spectre issues and offshoots such as Hertzbleed, if malware really wants to steal data, there are generally enough of vulnerabilities in operating systems and programs to do so, or methods to socially engineer the user without compromising the host CPU.
"Unlike its siblings, who trigger harmful branch target speculation by exploiting indirect jumps or calls, Retbleed exploits return instructions," explained Wikner and Razavi in a draft blog post about the design bug provided to The Register. "This means a great deal, since it undermines some of our current Spectre-BTI defenses."
AMD Zen 1, Zen 1+ and Zen 2 were found to be affected. Newer Intel CPUs up to Alder Lake also suffer from Retbleed through BHI, another vulnerability that was disclosed earlier in the year, but exploitation is harder
Retbleed: A new Spectre version infects older Intel and AMD CPUs.