A new ransomware variant is spreading and the second one in a short timeframe for QNAP. It encrypts QNAP NAS servers in return for a payment in bitcoin to decrypt them. The ransomware makes use of a zero-day vulnerability that allows it to bypass two-factor authentication.
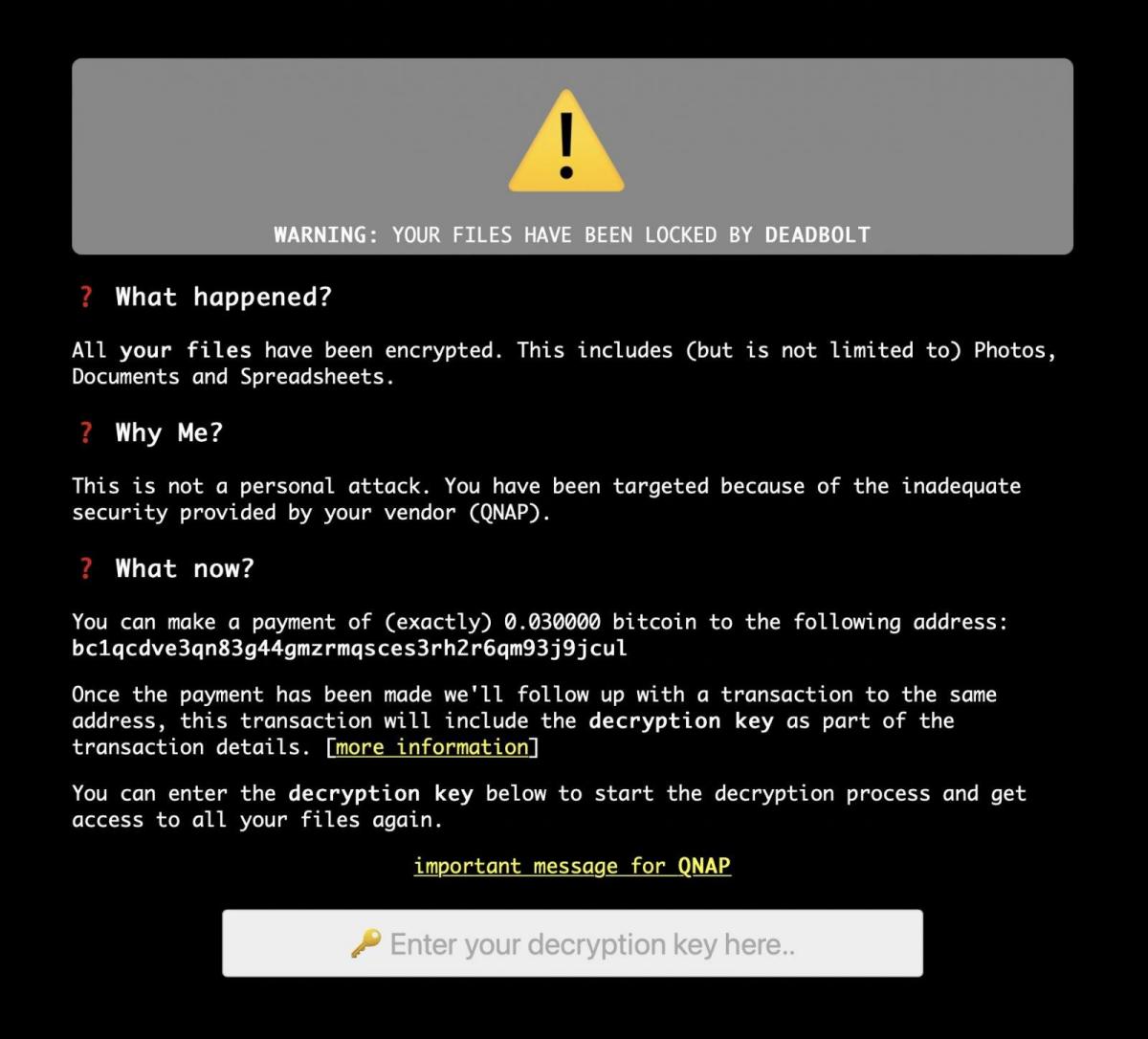
The attacks began January 26th reports bleeping computer, when QNAP devices discovered their data had been encrypted and their file names had been prefixed with a.deadbolt file suffix. Rather than placing ransom notes in each folder on the device, the QNAP device's login page is hijacked to display a message that reads, "WARNING: Your data have been encrypted by DeadBolt," as illustrated in the image below. This screen instructs the victim to send 0.03 bitcoins (about $1,100) to an enclosed Bitcoin address that is unique to each victim.
Basically QNAP want you to disable passing data over the web by closing all ports on the WAN side.
Taipei, Taiwan, January 26, 2022 - QNAP® Systems, Inc. (QNAP) today issued a statement in response to a new type of ransomware named DeadBolt. DeadBolt has been widely targeting all NAS exposed to the Internet without any protection and encrypting users’ data for Bitcoin ransom. QNAP urges all QNAP NAS users to follow the security setting instructions below to ensure the security of QNAP NAS and routers, and immediately update QTS to the latest available version.
Check whether your NAS is exposed to the Internet
Open the Security Counselor on your QNAP NAS. Your NAS is exposed to the Internet and at high risk if there shows “The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP” on the dashboard. If your NAS is exposed to the Internet, please follow the instructions below to ensure NAS security:
Step 1: Disable the Port Forwarding function of the router
Go to the management interface of your router, check the Virtual Server, NAT or Port Forwarding settings, and disable the port forwarding setting of NAS management service port (port 8080 and 443 by default).
Step 2: Disable the UPnP function of the QNAP NAS
Go to myQNAPcloud on the QTS menu, click the “Auto Router Configuration”, and unselect "Enable UPnP Port forwarding".
QNAP NAS systems vulnerable to new ransomware
.png)