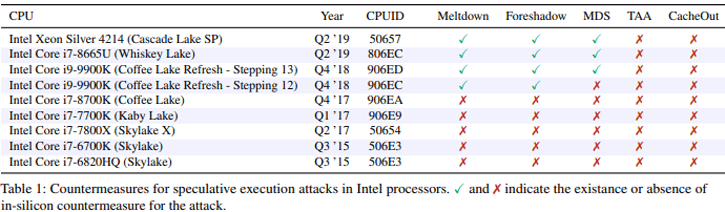
Intel is not spared when it comes to the number of vulnerabilities that keep hitting their processors. The latest one is CacheOut, a new speculative execution attack that is capable of leaking data from Intel CPUs across many security boundaries. All processors up-to-the recent Coffee lake refresh are effected.
Despite Intel's attempts to address previous generations of speculative execution attacks, CPUs are still vulnerable, allowing attackers to exploit these vulnerabilities to leak sensitive data. Unlike previous MDS issues, the researchers show in their work how an attacker can exploit the CPU's caching mechanisms to select what data to leak, as opposed to waiting for the data to be available.
They then demonstrate that CacheOut can violate nearly every hardware-based security domain, leaking data from the OS kernel, co-resident virtual machines, and even SGX enclaves. CacheOut can bypass software fixes. Making it possible to extract data from both the kernel of the OS and from virtual machines, and also from something that Intel calls 'software guard extensions' (SGX) that normally is stored securely.
Researchers from the University of Michigan and the University of Adelaide have found this new bug, and posted a paper on it. Read the paper. It seems that once again only Intel processors are affected including Core, Xeon and Atom models. AMD is save from this vulnerability.