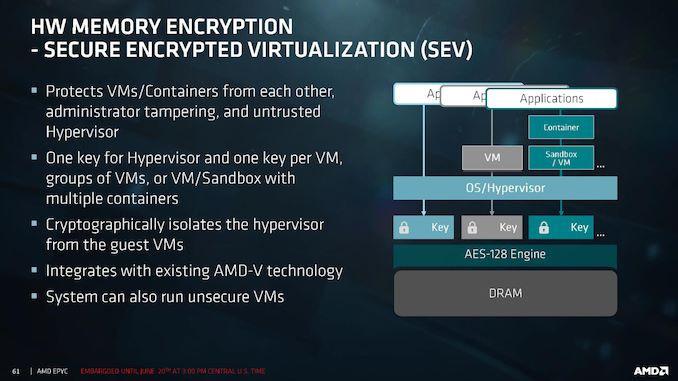
A month or so ago. Cfir Cohen, a member of the Google Cloud security team, alerted AMD about a problem with the Secure Encrypted Virtualization (SEV) functionality of the Epyc processors. This vulnerability could allow an attacker to intercept a secret key that could give access to isolated virtual machines.
This specific vulnerability has been patched but did require a firmware update. The update is named CVE-2019-9836 and it is of course strongly recommended to install that update as quickly as possible. The news about the leak was announced after the problem could be identified and resolved, and that's the way it should go.
At AMD, security remains a top priority and we continue to work to identify any potential risks for our customers. Through ongoing collaboration with industry researchers AMD became aware that, if using the user-selectable AMD secure encryption feature on a virtual machine running the Linux operating system, an encryption key could be compromised by manipulating the encryption technology’s behavior. AMD released firmware-based cryptography updates to our ecosystem partners and on the AMD website to remediate this risk.
AMD addresses SEV security vulnerability in Epyc CPUs with firmware update